In On the Mode of Existence of Technical Objects (1958), French philosopher Gilbert Simondon noticed that humans were losing their reciprocal connection with technology. We push buttons without understanding what’s happening ‘inside’ the machine – whether it’s a light switch or a smartphone. ‘For Simondon, restoring this mutual relationship would be a means for developing a technological culture’, says computer scientist and philosopher Yuk Hui. Revealing the different structures of a technology, which are ‘inside’ the machine, can reduce technical alienation. ‘An individual technical object can’t exist without a wider associated milieu’, states Hui. Thus, we need to look at its mechanisms, infrastructures and physical manifestations.
Developments in financial technologies envision a machine-controlled economy. On the one hand, this enables us to trade goods and services at the touch of our fingers. On the other hand, ‘[o]ur ability to exchange without knowing where things come from blinds us to the real core of the economy’, notes financial activist Brett Scott. How do financial technologies alienate us from the exchange when it’s depicted as code on a computer screen? How do these encrypted languages shape our society? In this case study I will investigate the materiality of cryptocurrency through the lens of product design. Cryptocurrency is virtual money that uses cryptographic systems and records its transactions via a distributed ledger technology, typically a blockchain. I will research cryptocurrency through design and in doing so give shape to intangible technology. The product design concepts presented in this article will help build a bridge between cryptocurrency and culture, and will mitigate our technical alienation from the impact of cryptocurrency transactions.
Enlarge
The Crypt of Cryptocurrency
Information is easily transmittable when it is compact, discrete and modular. Hashing is the cryptographic process of turning an unlimited amount of input data into a fixed amount of output code. The process converts payment details into a compact hash which corresponds to a 5-figure number known as the nonce. When someone tries to corrupt the data the hash-nonce combination won’t match, which instantly reveals any fraudulent activity. The complexity of encryption makes it nearly impossible to decrypt a hash and uncover the original message. Hence, if you compute a hash for a password, you can safely store the hash without exposing the private data. Additionally, each block on a blockchain contains the hash of the current and previous block to verify the provenance of the money. If a malicious person changes the amount of money or double-spends it, the block ceases to correspond to the other blocks. A single blockchain is saved in multiple places so you can compare each copy and detect the deviant blockchain-copy.
Mining is the process of verifying transactions by solving cryptographic puzzles. A miner is a machine that repeatedly computes numbers to confirm transactions. The transfer is approved when the miner finds a correlating hash-nonce combination, which starts with a predefined number of zeros. In return, the miner receives a reward. Additionally, the system can automatically raise the computational difficulty by increasing the required number of zeros. This ensures that the verification will always take ten minutes, whether the computing power is high or low. Whereas the natural scarcity of a material (e.g., gold) causes its value to rise, cryptocurrency ensures an artificial scarcity by regulating the difficulty of the code.
If Alice wants to transfer cryptocurrency to Bob, she has to know the public key of Bob’s digital wallet. A public key is mathematically paired to a private key and together gain access to a digital wallet that holds cryptocurrencies. The trapdoor function makes it easy to compute a mathematical function in one direction, yet difficult to compute in its opposite direction. It guarantees that it’s nearly impossible to deduct the private key if you know someone’s public key. When transferring cryptocurrency, you aren’t literally sending a coin to someone; it is merely addition and subtraction. Alice’s wallet loses a coin and Bob’s wallet gains a coin. Transactions process this conversion and a blockchain records the rearrangement of the possessions. In essence, you solely possess a 34-character public key and 64-character private key that authorize your access to the value. Although cryptocurrency entails numerical functions and depictions, these cryptographic schemes require ‘particular arrangements of individuals and institutions (…) Such social arrangements are obviously not products of mathematics’, argues Quinn DuPont in his archeological study on cryptography. The collective adoption maintains a fundamental feature of the technology.
Cryptocurrency can be obtained in a variety of ways – from using a credit card at an online broker to trading it with cash via alternative crypto-cash services. Purchasing cryptocurrency anonymously is challenging due to the transparent nature of blockchain technology. ‘[W]ith strict KYC/AML regulations in place in most international exchanges and blockchain analysis companies such as Chainalysis and BlockSeer, bitcoins may now be easier to trace than cash’, as explained on Crypto Insider.
As part of this research I set out to buy my own cryptocurrency. I preferred to stay anonymous – or rather pseudonymous – and I wanted to physically experience the exchange. A cryptocurrency ATM enabled me to trade cash for cryptocurrency. Nonetheless, I still had to search for these particular ATM’s online because their presence in the city is unknown. The nearest one was located inside Lucky Jack’s casino in Amsterdam. Their General Bytes ATM exchanges three cryptocurrency types: Bitcoin, Litecoin, and Ether. Although I inserted €20, I only received €14,66 worth of bitcoins in return (the transaction took place on May 7, 2018). Why did I lose more than a fourth of my money? The paper receipt solely verified basic information of the transaction but excluded the calculations. During a phone call with the ATM operator, he explained the numerous fees involved in the crypto-cash exchange. I came to realize that anonymity comes with a price. It puzzled me that neither the ATM nor the receipt displayed the complete description of the fees. Receipts prove that something is received but with virtual currency that ‘something’ turned out to be rather nebulous. What does the seamless interface of the Automated Teller Machine hide for us? How can we redesign the receipt to decode the transaction?
Enlarge

In the words of Gilles Deleuze, we have to look for new weapons in our societies of control. As a weapon cryptocurrency controls and orders our society, but in what respect? Due to the digitization and automation of monetary systems, various human actions delegate to financial technologies (the word delegation refers to Bruno Latour’s actor-network theory). With this approach Latour describes the manner in which humans give agency to non-human actors (i.e., technology). How do we shape a technological device? Which actions and behaviors will it have and how does it shape us in return? We will perceive the mechanisms of cryptocurrency with this idea of delegation to reconnect digital processes to the human input that preceded it.
Previously cash moved from hand-to-hand but with cryptocurrency the transfer is automated. Computerizing the transmission of money has its benefits: we can schedule transactions whenever it suits us, we don’t have to carry the money around, and we don’t have to physically hand it over to the receiver. At the same time this change detaches us from the processes, imposes us to blindly obey the procedures, and transfers money through superficial user interfaces. With our hands off the wheel, we will become passive ‘operators’ and the ‘servant of the machine’ (to recall Simondon) who rely on the technology to function and availability of customer support when it fails. Thus, in line with Simondon, it’s arguable whether automation is a gift or a limitation since it creates an unbalanced relation between technology and humans. Should we allow automation to be dominant? Are machines truly autonomous? If not, how are they controlled and by whom?
Furthermore, the technology substitutes physical labor with digital labor. Traditional trade requires us to work for money, but with cryptocurrency we can now let the computer do the work for us using mining algorithms. As a result, we won’t be able to compare the products we buy with the amount of time we had to work for it. How will this delegation reshape the meaning of value? Will tangible objects still hold the same value as digital objects? To clarify these questions, ‘we must go back to “the things themselves”’, as claimed by philosopher Edmund Husserl in Logical Investigations. We must return to the individual aspects that are part of financial technologies before we delegate transactions to machines, since ‘technology registers reality in advance of meaning’, says DuPont.
Phase of Transition
A block on a blockchain verifies a transaction through cryptography. While the façade of a block merely shows general data, its physical manifestations are left unseen. How does the transaction manifest itself in the physical environment? How can a material bear witness to a cryptocurrency transaction? This notion of a material witness, coined by Susan Schuppli of the Centre for Research Architecture, denotes ‘an entity (object or unit) whose physical properties or technical configuration records evidence of passing events to which it can bear witness.’ Such an evidential agent provides a concrete yet encoded proof of an external event. A material can witness an event directly, for example, when snow turns black due to carbon-polluted air. Also, it can indirectly witness an event via an apparatus, for instance, when a film camera captures radiation onto its film (see figure 3). ‘The Most Dangerous Film in the World’, to cite Schuppli, was made from a helicopter that was flying over Chernobyl’s nuclear reactor. The camera operator assumed that the black dots were defects that arose during the development of the film. Afterward, it became evident that those dots were the consequence of radiation. The meltdown of Chernobyl was captured by the physical properties of the 35-mm film roll.
Enlarge

A material witness can produce a physical verification of the cryptocurrency transfer. It will capture the fingerprint of the transaction, the phenomenon of the code, and the crystallization of the computational processes. Consequently, this receipt won’t merely visualize code but retraces the code back to its materiality. The technology, nevertheless, is part of a larger ensemble and requires an arrangement of external elements – which we shouldn’t obscure. As archeologists, we will excavate the strata of cryptocurrency through the reading of Yuk Hui’s book On the Existence of Digital Objects. In his book, Hui analyzes the ‘orders of magnitude’ of a digital object to reveal its layers of abstraction. He aims ‘to produce a system of thoughts that bridges different orders of magnitude through developing a theory of relations.’ We will narrow down the theory of relations to interobjectivity, which concerns the relationship between an object and its environment. Hui explains that ‘[t]he order of magnitude also designates an approximation or imprecision, meaning that it is impossible to fully analyze the world with absolute precision’. Therefore he didn’t examine every order of magnitude but went from ‘code to phenomena’. Following his reasoning I will examine the code of a transaction from the mining process (computation) to the verified block on a blockchain (human experience).
What happens when we transfer cryptocurrency? What happens when the data is neither located at the sender nor the receiver? During this phase of transition, cryptocurrency is in a state of individuation – not to be confused with individualization. According to Hui, ‘individualization demands a hierarchy that puts different elements into a functioning order, whereas individuation produces, not a hierarchy, but rather a “hierarchical relativity”.’ In other words, we will not define the transaction from start to finish, but rather inspect the fluid and unstable state of the exchange – the individuation. During this process, dichotomies fade without omitting one or the other. The individuating cryptocurrency is located in-between the sender and the receiver, medium and message, technology and society. The ‘resolution of tensions’ in this hybrid form can be retraced by observing the transaction with a material witness (see figure 4). Throughout the transaction, the computer has to perform binary procedures that cause the hardware to rise in temperature. The actual material (in this case, a copper sheet) absorbs these heat fluctuations, and thus bears witness to the individuating cryptocurrency.
Reimagining the Transacion
Why do we approach the question of the existence of digital objects from the perspective of data? True, these objects appear to human users as colorful and visible beings, yet at the level of programming, they are text files; further down the operational system, they are binary codes, and finally, at the level of circuit boards, they are nothing but signals generated by voltage values and the operations of logic gates.
YUK HUI, ON THE EXISTENCE OF DIGITAL OBJECTS
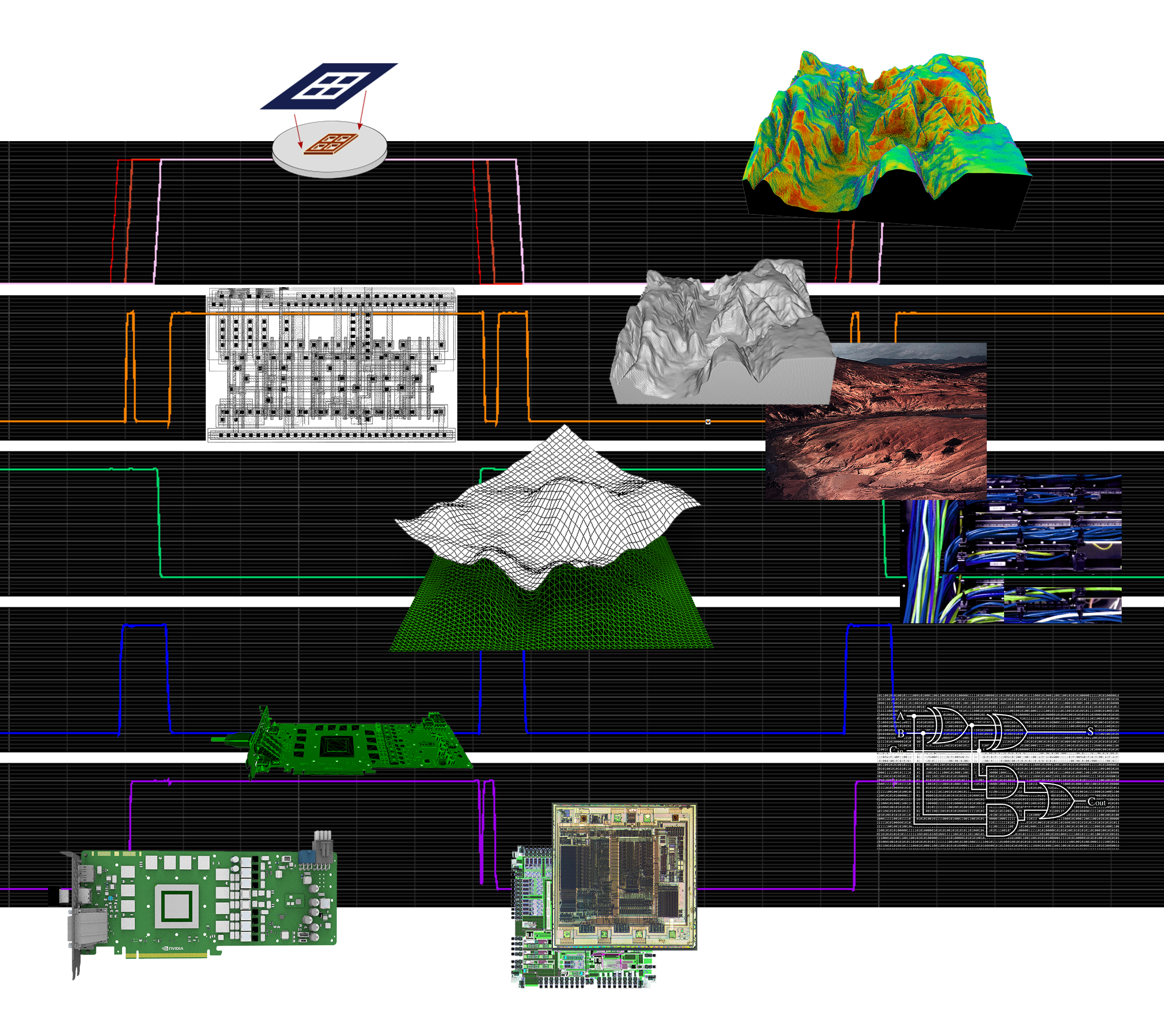
What does a cryptocurrency transaction look like from the perspective of the signal? When using cryptocurrency, the code of the transaction is the single data at presence. Since information obeys essential laws of physics, according to ‘the father of information theory’ Claude Shannon, we should look beyond code and examine the electrical signals of cryptocurrency – the physics of the code. In essence, when electricity flows through the circuit board the computer recognizes a ‘1’ and when electricity can’t flow the computer recognizes a ‘0’. Through these two states it becomes possible to compose code that can represent value and its transferal. During the act of mining, the signal of cryptocurrency is scattered around because the miner tries to find a corresponding hash-nonce arrangement. The computer starts to compute and sifts the noise into the correct signal. After filtering the noise, the resulting signal depicts the digital value at its new address.
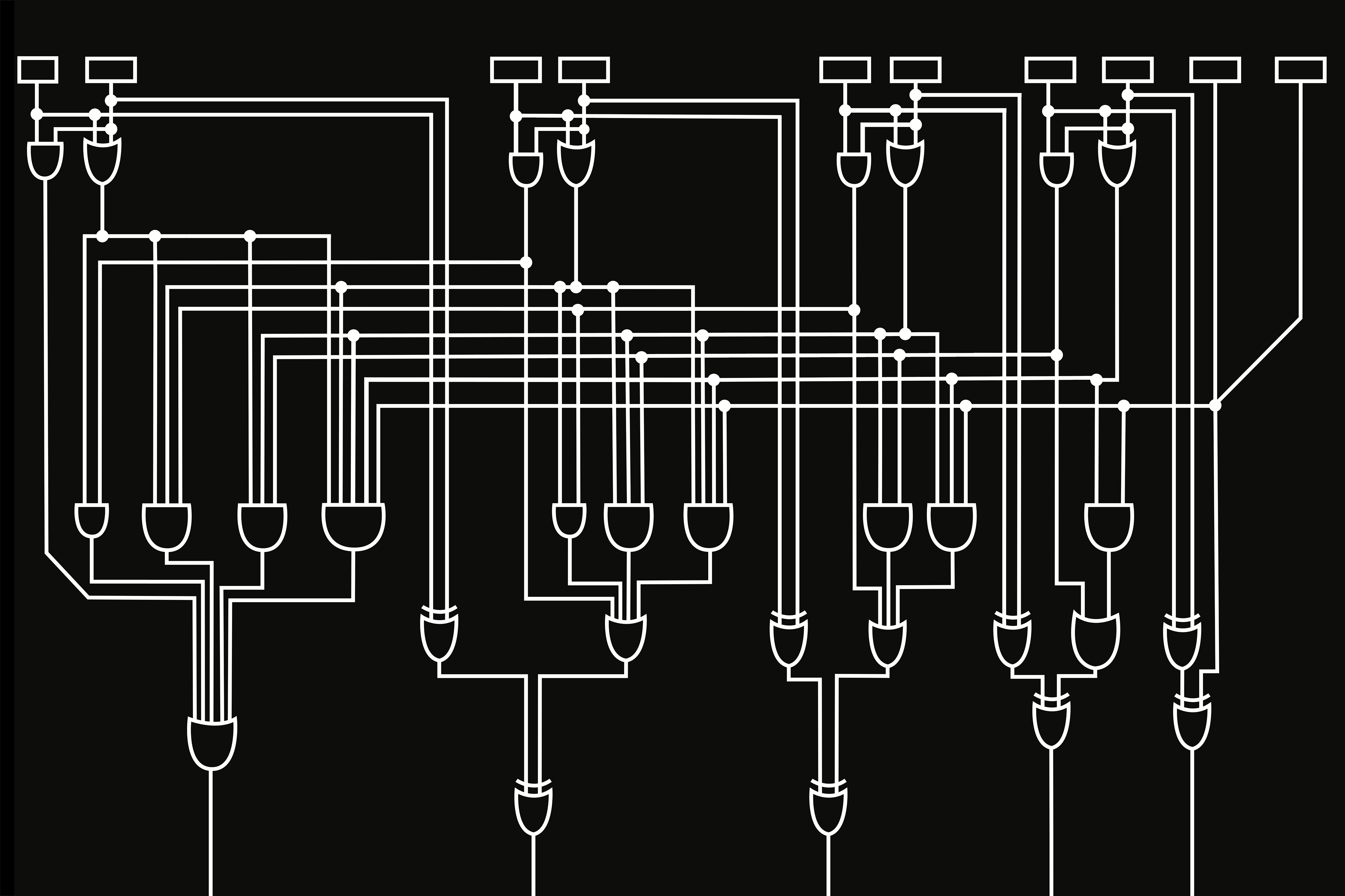
Further down the line these flows have to be conducted through the conduits of computer chips. Microscopic layouts are etched into the circuit board and create copper paths that steer the electricity. These nanofabricated pathways enable myriad outputs since each path leads to a set of code. Electricity pulses through these paths until it finds the route that confirms the transaction. An example of a layout is the full adder design, which empowers the computer to measure signals. A sequence of full adders produces a carry-lookahead adder that – as the name implies – looks ahead and anticipates the flow of electricity (see figure 5). It predicts the sum before it is calculated. The carry-lookahead adder is crucial for cryptocurrency since it concerns the prediction of code – in other words, the extrapolation of value. The significance of these abilities is evident in high-frequency trading where algorithms use their speed to trade ahead of price increases. Virtual transactions require material conversions and the computer’s pace to process the code influences the profit. The dictum ‘time is money’ still applies here.
Enlarge
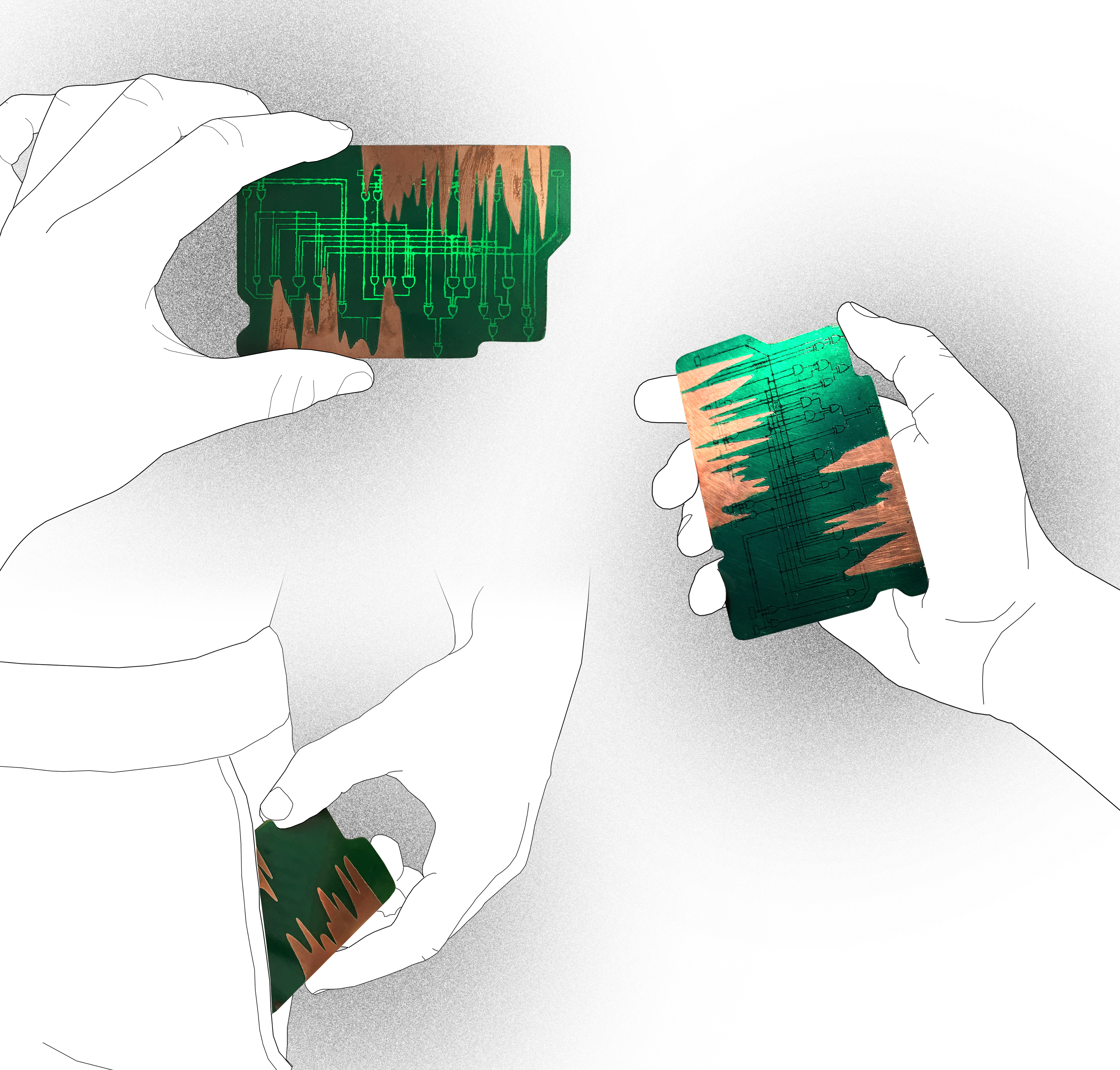
Observing the orders of magnitude allow us to form a sensible understanding of the technology. The two resulting prototypes become the screenshots of these energetic computational activities. They physically capture the transmission of cryptocurrency and become the proof of the transaction (see figure 6). A printed circuit board is used as the medium to retrace the matter of the transaction. Electrical waves overflow the circuit board and bare its raw layer of copper – the precious metal with its conducting abilities. The prototype on the left proves my personal transaction. Its longest signal (upper left) denotes the hash that verified the transaction and the shorter signal denotes my public key. The back of this prototype (lower left) denotes the two public keys of the ATM – the provenance of the transaction. The prototype on the right proves the first Bitcoin block ever mined; hence the rear (lower right) is empty because there wasn’t a previous owner. The hash signal of the genesis block (upper right) starts with less consecutive waves (i.e., the number of zeroes) than my personal transaction because Bitcoin’s difficulty was noticeably lower in 2009.
Enlarge
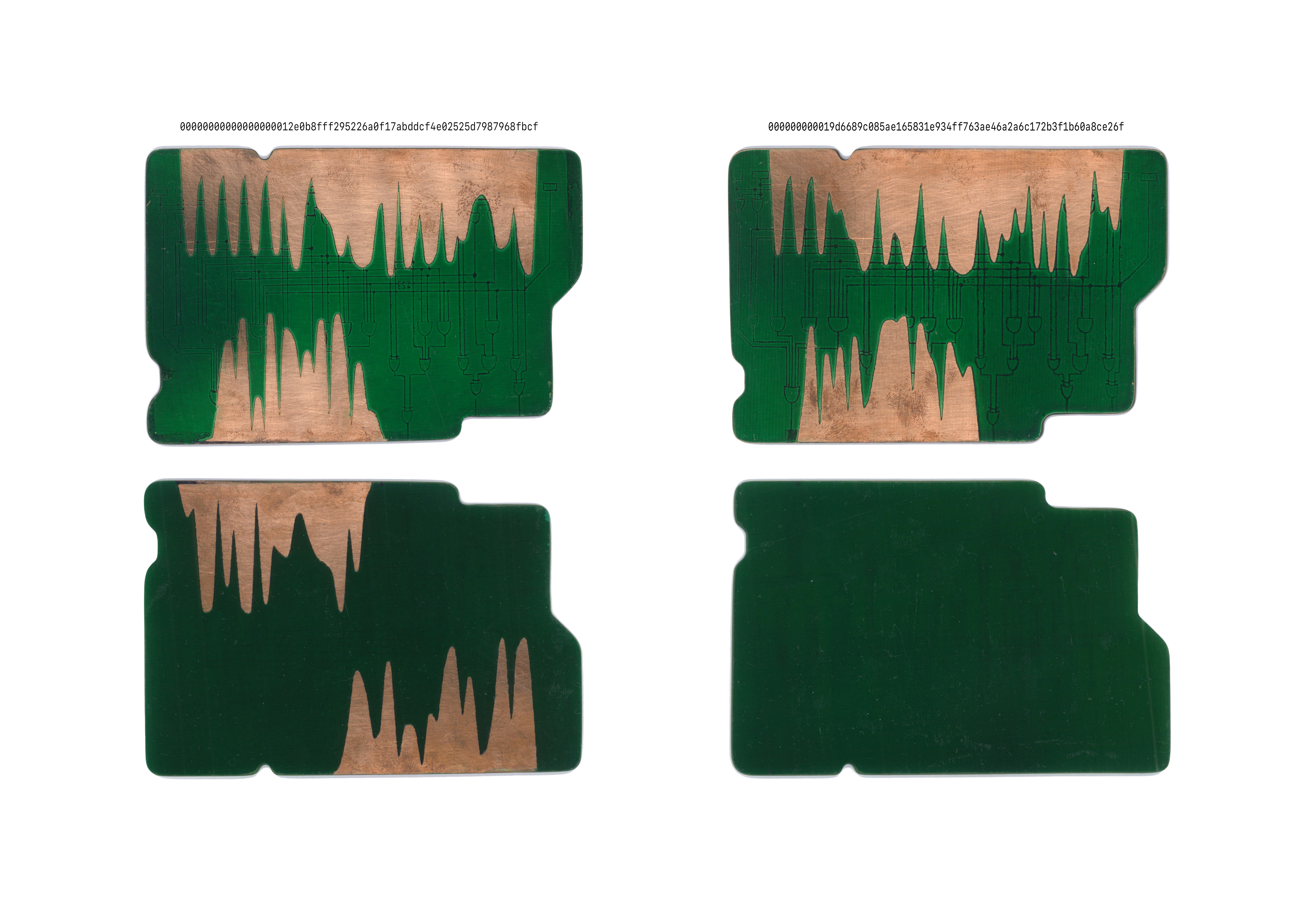
Besides rewiring the transaction to its materiality, the prototypes describe the technology through its relations. The interobjective relations are twofold: on the one hand, the object coexists with its environment, on the other, the object’s physical layers relate to each other as well. The computational complexity synchronizes itself to the quantity and quality of the mining-network. When fewer people participate in Bitcoin, the difficulty and demand will decrease, as would its value. These changes also affect the manufacturing process of mining hardware and the necessity of raw materials. Compute-intensive tasks exhaust the material quickly and require enhanced thermal architectures. Furthermore, the circuit board comprises three observable layers: bare copper, conduits and green lacquer. Whilst the coating laminates the mechanisms, the tokens bare themselves on the surface. For Hui, the formation and accumulation of relations is the essential task of digital technologies. Without interobjectivity, signals and code remain formless.
Proof of Transaction
Through redesigning the cryptocurrency transaction receipt, a new notion emerged. Proof-of-Transaction is a physical object that absorbs the process of transferring value from one space or entity to another. It captures the orders of magnitude of the exchange (from technology to phenomena) and narrates these realities through interobjective relations. The concept uses the Latin root of the word ‘transaction’ (transactio), meaning ‘an agreement’. The agreement involves an exchange or interaction between two entities. The word ‘proof’ is regarded as ‘evidence’, the witness of an event. Proof-of-Transaction explores the manner in which we experience the exchange of value and delves into the relationship between value and things. A thing can be paper money or a piece of code, but (more broadly speaking) encompasses activities, assistance or cooperation. Things encapsulate value, but when things become immaterial it becomes difficult to retrace the value. The reimagined cryptocurrency receipt concentrates on cryptocurrency (as a type of value), and therefore can be seen as an example of the notion Proof-of-Transaction.
How does Proof-of-Transaction compete with two other canonical consensus algorithms of cryptocurrency? As described by TechTarget, ‘[a] consensus algorithm is a process in computer science used to achieve agreement on a single data value among distributed processes or systems.’ The first consensus algorithm is Proof-of-Work (PoW), which is performed through mining and used by Bitcoin, Litecoin and Dogecoin among others. The miner is incentivized because it receives a reward for solving the puzzle that verifies the transaction. The quantity and quality of the computer determine the mining power and consequently the profit you can make. PoW reaches consensus because the miner has to (literally) prove the verification through computational labor, and at least 51% of the miner-network has to agree with the verification.
The second consensus algorithm, Proof of Stake (PoS), selects a validator (comparable to a miner) based on the number of coins it deposits. Since one validator verifies the transaction, you don’t need to waste as much energy and hardware as Proof-of-Work – where each miner tries to solve the same transaction. However, the rich get richer as they have higher chances at the selection procedure, meaning higher chances to receive the reward. PoS is implemented by Peercoin, Decred, and Ethereum. This verification scheme reaches consensus because the validator-network checks the reviews as well. The validator won’t verify fraudulent transactions because it will lose more money (the deposit) than it can earn (the reward).
How do we build trust in these invisible algorithms? How can we agree on unproven mathematical assumptions without nourishing speculation? Proof-of-Transaction reaches consensus because it records these concealed procedures through its analog properties. It retraces computation to its physics to provide evidence of the exchange. The intangible exchange of value is unified with its source and encapsulated by the object. Although the algorithms and transactions are dynamic, the embedded proof remains static. As a result, when a cryptocurrency activity or value changes, it won’t coincide with the appearance of the Proof-of-Transaction. Furthermore, the capturing of the signal is infinite and can adapt to the changing complexity of the code.
Technical Alienation
“[A]bandoned, scammed, website dead, no nodes, wallet issues, no social updates, low volume or developers have walked away from the project.”
COINOPSY, LIST OF DEAD COINS
After developing Proof-of-Transaction, the prototype was used as the basis for a speculative scenario that sheds lights on its potential applications. This future situation will ‘tell a story about the world in which that technology is situated’, as explained by design researcher Joshua Tanenbaum in Design Fictional Interactions. Our scenario portrays Proof-of-Transaction as a physical cryptocurrency wallet (figure 7). Instead of capturing the code of the transaction, the wallet captures the public and private key. Security is increasingly strained due to the rise of interconnected and high-speed devices. The protection of your digital treasures becomes increasingly difficult. Turning your device off will not prevent a malicious person accessing your private data. When the value is stored physically this particular risk is mitigated and subsequently the storage acts as a mnemonic device, reminding the users of their keys and its tangible existence. At this stage, the wallet predominantly functions as a thinking tool rather than a finalized product that is ready to be adopted by the mass. It is a means to evoke discussions, questioning, and action on user experiences with cryptocurrency. How should we design interfaces between value and society? How can we use the tangibility of product design to enrich the conception of the technology? Can a physical wallet incentivize users to engage with the technology more actively?
Enlarge
Film scholar David Kirby coined the term diegetic prototype to describe ‘cinematic depictions of future technologies (…) that demonstrate to large public audiences a technology’s need, benevolence, and viability.’ Tanenbaum uses this term in regard to Design Fiction because ‘[s]ituating a new technology within a narrative forces us to grapple questions of ethics, values, social perspectives, causality, politics, psychology, and emotions.’ We will create a diegetic prototype to depict the technical alienation caused by the possible future dominance of financial technologies.
Virtual currencies became the standard of value and used unconsciously. We blindly trust code without understanding its provenance and influence. Suddenly, the system freezes. Money stopped flowing, wallets are rinsed and memorized keys drained away.
As a last resort, the protagonist starts a dialogue with Siri in search of clarifications. Siri doesn’t understand the questions and responds metaphorically: ‘Your keys are in the cloud.’ But where can we find this so-called cloud? Why can’t we access our wallet? And who or what is responsible for the disruption? After precisely 10 minutes, lo and behold, the system starts working again. The artificial scarcity (inherent to Bitcoin) manipulated the flow of money and controlled our behaviors in return. In agreement with Hui, we can argue that ‘[t]he user’s role in a preprogrammed context is always already anticipated, if not totally programmed.’ If this preprogrammed system crashes, do we still know how to reset it? What if a technical failure wipes out every cryptocurrency and leaves us behind with a digital tabula rasa? Do we want to live in automated environments in the first place?
Proof-of-Transaction prescribes that financial technologies capture reality by combining cryptocurrency and culture. It requires acknowledging that cryptocurrency isn’t digital value, but value through the medium of the digital. The value is bound by material and social assemblies and mediated by Liquid Crystal Displays. Through the concept, we can explore relationships between technical objects and its environment. Nevertheless, it is important to note that this new notion isn’t solely restricted to our exchange of value. A machine-to-machine economy foresees automatons exchanging value – from data to cooperation – without human interference. In such a network, machines pool their resources via blockchains and smart-contracts. As explained in Blockchain Revolution, ‘[h]umans animate the agents, endowing them with computing power and capital to go about their work. They buy the services they need, hire people or robots, acquire partner resources (…) and adapt in real time.’ We bring these self-steering financial entities into existence but do we know how to remain in touch with it? How can Proof-of-Transaction encourage us to use these machines as balanced users instead of mere operators? Perhaps we need to think beyond our western perspective, beyond the culture/nature dualism and start exploring financial technologies through distinct cosmologies. How can Amerindian Perspectivism and Japanese Techno-animism complement our comprehension of technology? Can we see technology as a living organism? For now, let us start with reimaging cryptocurrency by thinking beyond code.
Tim Brouwer (NL) holds a BSc in Product Design from the Amsterdam University of Applied Sciences and is a candidate for the MA Research Architecture at Goldsmiths University of London. The longform is derived from Brouwer’s thesis for the bachelor Product Design in cooperation with the MoneyLab project run by the Institute of Network Cultures.
References
Coinopsy, https://www.coinopsy.com/dead-coins/.
Deleuze, Gilles. Postscript on the Societies of Control, Vol. 59, pp. 3–7, The MIT Press, 1992.
DuPont, Isaac Q. An Archeology of Cryptography: Rewriting Plaintext,
Encryption, and Ciphertext, PhD diss., Faculty of Information, University of Toronto, Canada, 2017.
Hui, Yuk. On the Existence of Digital Objects, Minneapolis and London: University of Minnesota Press, 2016.
Husserl, Edmund. Logical Investigations Vol. 1, trans. J.N. Findlay, London: Routledge & Kegan Paul, 1970.
Kern, Michael. ‘Beyond the headlines: A look at two conflicting bitcoin theories’,
https://cryptoinsider.21mil.com/beyond-headlines-look-two-conflicting-bitcoin-theories/.
Kirby, David. ‘The Future Is Now: Diegetic Prototypes and the Role of Popular
Films in Generating Real-World Technological Development’, Social Studies of Science 40, Issue 1, Manchester: SAGE Journals, 2009.
Latour, Bruno. ‘Where Are the Missing Masses? The Sociology of a Few Mundane Artifacts’, 1992, http://www.bruno-latour.fr/sites/default/files/50-MISSING-MASSES-GB.pdf.
Rouse, Margaret. Consensus Algorithm, https://whatis.techtarget.com/definition/consensus-algorithm, 2017.
Schuppli, Susan. Material Witness, http://susanschuppli.com/research/materialwitness/.
Shevchenko, Vladimir. Chernobyl: Chronicle of difficult weeks, Russian Press Service, 1986.
Scott, Brett. ‘Riches beyond belief’, Aeon, 28 August 2013, https://aeon.co/essays/so-you-want-to-invent-your-own-currency.
Shannon, Claude E. A Mathematical Theory of Cryptography, Memorandum MM 45-110-02, Sept. 1, Bell Laboratories, 1945.
Simondon, Gilbert. On the Mode of Existence of Technical Objects, trans. Ninian Mellamphy, Paris: Aubier, Editions Montaigne, 1958.
Tanenbaum, Joshua. ‘Design Fictional Interactions’,
https://www.researchgate.net/publication/272490351....
Tapscott, Alex and Tapscott, Don. Blockchain Revolution: How the Technology Behind Bitcoin Is Changing Money, Business, and the World, Penguin UK, 2016.