Introduction
Picture this. It’s 2017, we are the character @observer on one of freenode’s IRC channels, while Tz4R4, dchmp and B_All are watching the newest !Mediengruppe Bitnik hack with awe: if you type the title of the the Swiss artist duo’s new book into the search bar of a seller’s website, it creates a popup window on the site with their name, blocking access. (The title is a code injection.) Nothing could express DADA better, exclaims B_All to Tz4r4, while dchmp is busy copy-pasting lines of script graffiti on Facebook in order to achieve a resemblance to the Gioconda on the (anti)social media platform’s feed.
Enlarge

Do you think that Hanna Höch would have created her collages in Gimp? That Picabia would have used microcontrollers? That Rose Sélavie would have her tweets going viral? Or that Hugo Ball would have written a bunch of Wikipedia articles about the DADA movement? I definitely think so. Except that without them behind us, we wouldn’t have had and used all these tools the way we do now. This text is an attempt to demonstrate why. It starts out from the assumption that there is something eerily common in the workings of the historical avant-garde and of hacker cultures, and methodologically examines them from different angles to rationalize this assumption and look at how this close kinship brings about hacktivist artworks.
Hacktivism can be interpreted in the context of art history and activist practices in contemporary media art. As I will show in this essay, hacktivism and the historical avant-garde are comparable and might shed light on each other. I also observe source code as text in relation to the avant-garde’s attitude towards language and of hacker cultures to programming languages to demonstrate the overlap of their core values. My question is what insights does the existing theoretical framework of the avant-garde provide to understanding hacker cultures and especially hacktivism? And what does hacktivism mean to subversive endeavors in media art? How can the realization of these connections inform artists to create more relevant work in a contemporary wired environment?
A Very Short Introduction to Hacker Cultures
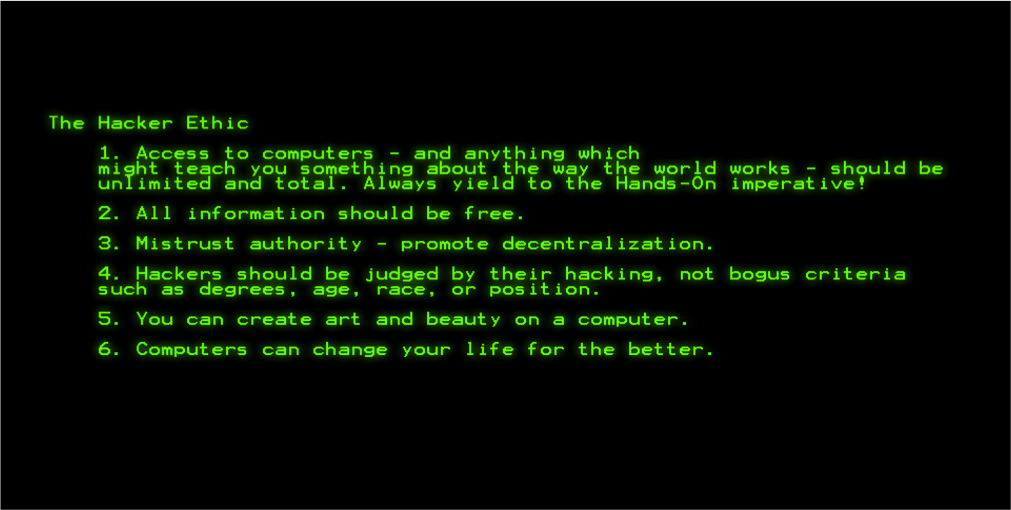
Hacking is best explored as a loose network of subcultures with a diverse history and a dispersed contemporary geography. As part of the history of digital culture, the history of hacker culture unfolded in connection with the closely interwoven technical, societal, and economic conditions of the late 20th century . The meaning of hacking changes through its rich history. Steven Levy defines a set of values as the hacker ethic, referring to early computer engineering communities. The six values are direct access, freedom of information, decentralization, meritocracy, the value of computer engineering ingenuity and aesthetics, and a general optimism towards computers.
Enlarge
Tim Jordan defines hacking according to technological determinism and distinguishes between hacking gestures based on their level of novelty and technological complexity: ‘Hacking creates new technological determinations by means of intervention, opposing an existing determination. Hacking is a material practice that produces change or novelty in the system of a computer, network, or communication technology.’
Jordan sees the continuity of the hacker ethic in hacktivism, as it intervenes into technological and societal determinations at the same time, thus changing how people interact with technology and each other. Hacktivism is the creation of new technological determinations, where these new determinations define interaction with technology in new and unexpected ways. Furthermore, hacktivism’s methods and goals are both collective, open and non-violent, aiming for political change. The determinations reformed by hacktivists are not only of technological nature but of cultural, economic, and communal character as well.
The Avant-Garde as a Precondition to Hacktivism
This essay proposes that the historical avant-garde of the 20th century played a major role in setting the stage for the intellectual framework of today’s hacktivism. Overcoming existing determinations and the creation of new ones was invented by the historical avant-garde and is now at the heart of hacktivism. In what follows I will dive into these parallels further.
The historical avant-garde was the first revolution in art that meant to attack, corrode, and question the institutions of art, its traditional genres and status in bourgeois society. The demolition of borders between art and life, the rejection of alienated artistic practice, and the invention of new practices are central to Peter Bürger's interpretation of the avant-garde's program in The Theory of the Avant-Garde.
We may find numerous analogies in the way avant-garde and hacktivism operates, such as their program of activism, their border violation practices, their performance and hacking instructions to be reconstructed by peers, their relations to tradition and invention, their questioning of individual authorship, and their provocative behavior towards mainstream society. Hacktivism overcomes technological determinations, in accord with hacker ethics, to create new modes of interaction and cultural attitudes. Those new interactions are not only non-conformist in their technological means, but in cultural attitude as well. Disrespect towards institutional, technological or societal authority is an apparent common element of avant-garde art and of hacker culture. They do not only question but oftentimes ignore authority, not only without respect, but with remarkable wit and amusement.
Claire Bishop identifies three major shifts of social paradigm in the history of Western European art: the avant-garde starting in 1917, the neo-avant-garde ending in 1968, and the fall of the Berlin Wall, along with the transition that followed. All the three social turns are the aftermath of a collapse of a vision of society. According to Bishop, these collapses are regularly followed by the re-articulation a Utopian rethinking of art’s relationship to the social and of its political potential. These attempts of re-articulation include the production, consumption and critique of art. These shifts, according to her, brought forth experiments to redefine art collectively, focusing on inclusion and cooperation. We see a similar process taking place in hacker culture in the nineties, just about the time of the third participatory paradigm shift (the fall of the Berlin Wall) identified by Bishop. Let’s examine the first shift to better understand this parallel.
The cult of novelty is of major importance to the avant-garde. Novelty in this regard is what circumvents institutions but is always instantly institutionalized. Helen Molesworth, in her study From Dada to Neo-Dada and Back Again, claims that the societal critique of Dadaism is a sublime failure, as the concept of artwork and the institutions resist all symbolic attacks against them without major difficulty. Kappanyos calls this the paradox of success. This paradox is omnipresent in hacker cultures any time someone previously attacking systems becomes an informant or a full-time employee of that same system. In this comparison to the avant-garde, the mainstream software industry resembles the novelty-hunger of art institutions.
Consequently, both the avant-garde and hacktivism depend on a status-quo to refer back to, to provoke, to expand or to question. Avant-garde artists provoke the canon and end up being canonized for the very same innovation. Hacktivists intervene in novel ways into an already existing system of a network, computer or communication technology. Both avant-gardists and hacktivists build their legitimization on a double basis: tradition and novelty.
Enlarge

Enlarge
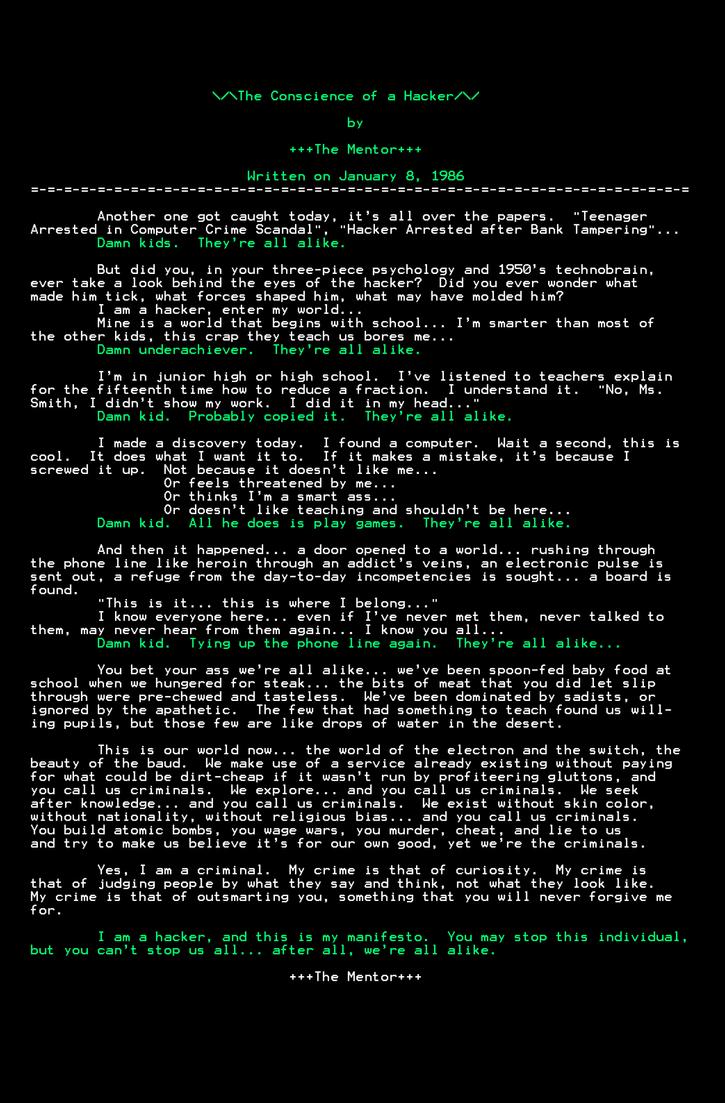
Both avant-garde and hacker culture refuse existing structures of the past/present in favor of an idealized future utopia. These tendencies show especially well in their common affinity for issuing ambitious manifestos. There is rarely a group or tendency of second-generation hackers without a manifesto declaring their ethics. General Public License for Free/Libre Open Source Software, The Cypherpunk Manifesto, the tech-critical Kaczynsky’s lifelong ambition of finishing The Unabomber Manifesto, The Conscience of a Hacker, the slogan of Anonymous, along with McKenzie Wark’s Hacker Manifesto, all appear with compositions of Utopian ethical standards aimed at the future. Just as the artists of the avant-garde, hackers also feel personally addressed to destroy borders and barriers that stand in the way of realizing their own autonomous ethic.
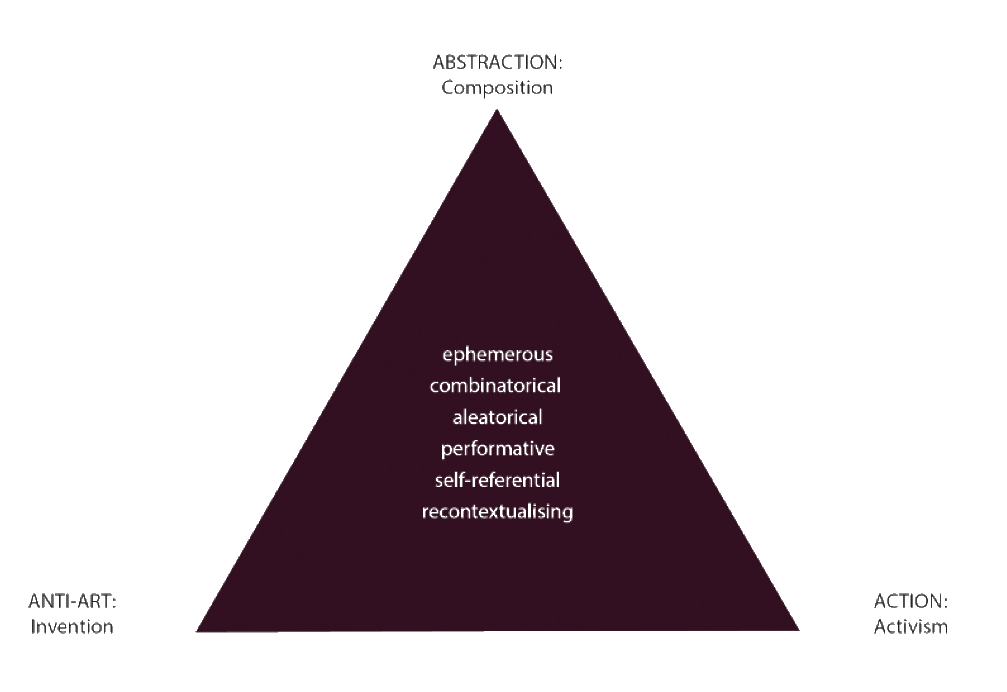
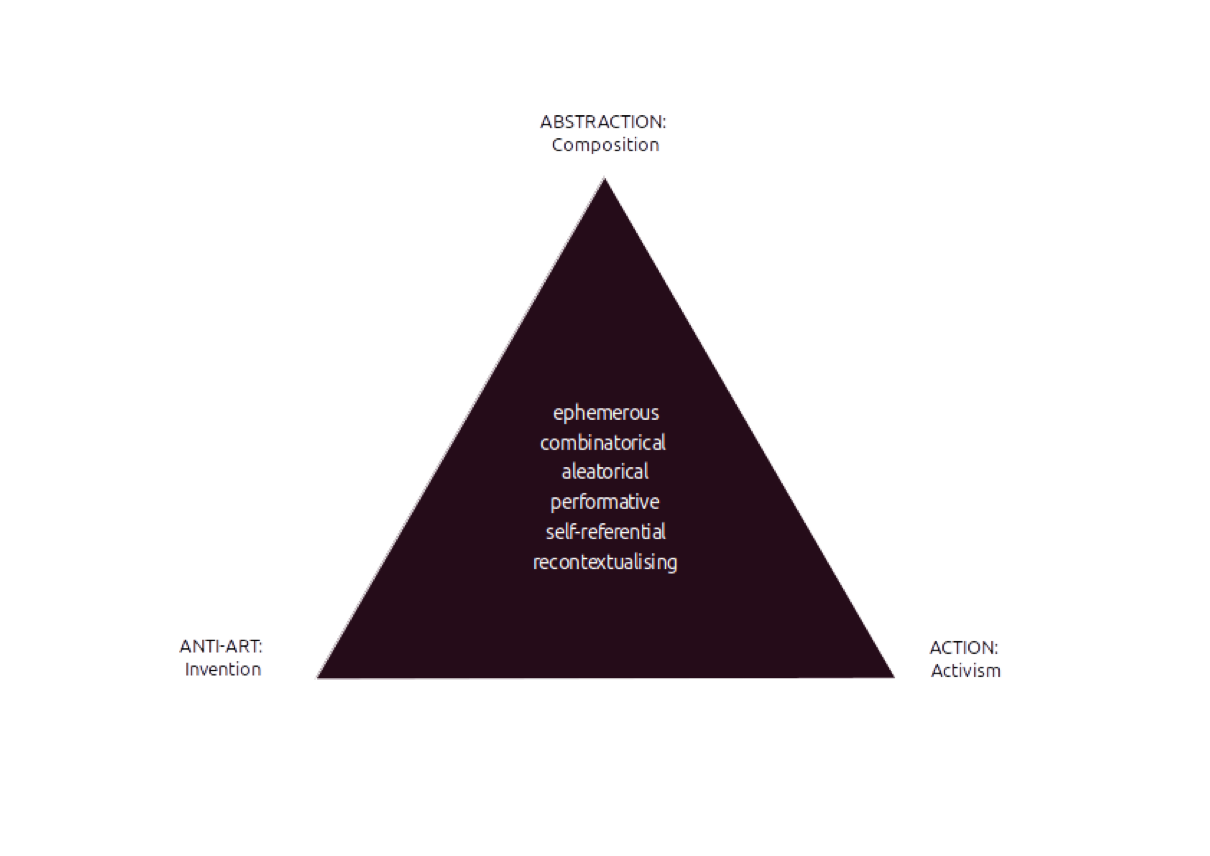
Kappanyos defines the framework for analysis of avant-garde strategies in the triptych of activism, abstraction, and anti-art, referring to composition, action and invention. He maps its many -isms as combinations of these factors’ variations. Let’s see how that applies to hacking.
Activism resonates in hacker cultures especially in the ‘Hands On Imperative’, in F/LOSS culture, and in the hacker work ethic. Hacker culture radically intervenes into political power structures, changes societal roles of info-technologies by making technology available to the public, previously an exclusive privilege of the military-industrial complex and academia. These practices do not only transgress borders of institutions, but borders between specialists (artist/hacker) and non-specialists (non-artist/ non-hacker/ public). In this regard, we may compare participation in case of a DDoS attack to that of a Cabaret Voltaire performance: in both cases, the specialist initiators (artists/hackers) act to change the behavior of a group of people that engages with them, in order to intervene into the societal/social status quo. The activity of the engaging group is a legitimate part of the hack or of the artwork, and through this engagement is the transgressive goal of the work fulfilled.
Abstraction, the liberation of composition from representation, is present in another statement of the hacker ethic: Code can be beautiful. Code is not only judged by its functionality, but by its linguistic value and structural elegance (within what particular language it is written in). This will be examined in the ‘Code is Speech’ part in more detail.
Actions of DADA and Fluxus are often recorded only by instructions, and are performed differently each time. Recipe-like instructions for performing action are not only a tradition of DADA and Fluxus, but of hacktivism as well: Anonymous and many other groups make their sets of instructions for performing a certain hack widely available to others. Instructions for reconstructable performativity play an instrumental role in F/LOSS and open hardware culture, such as online repositories and public documentation.
Enlarge

Enlarge
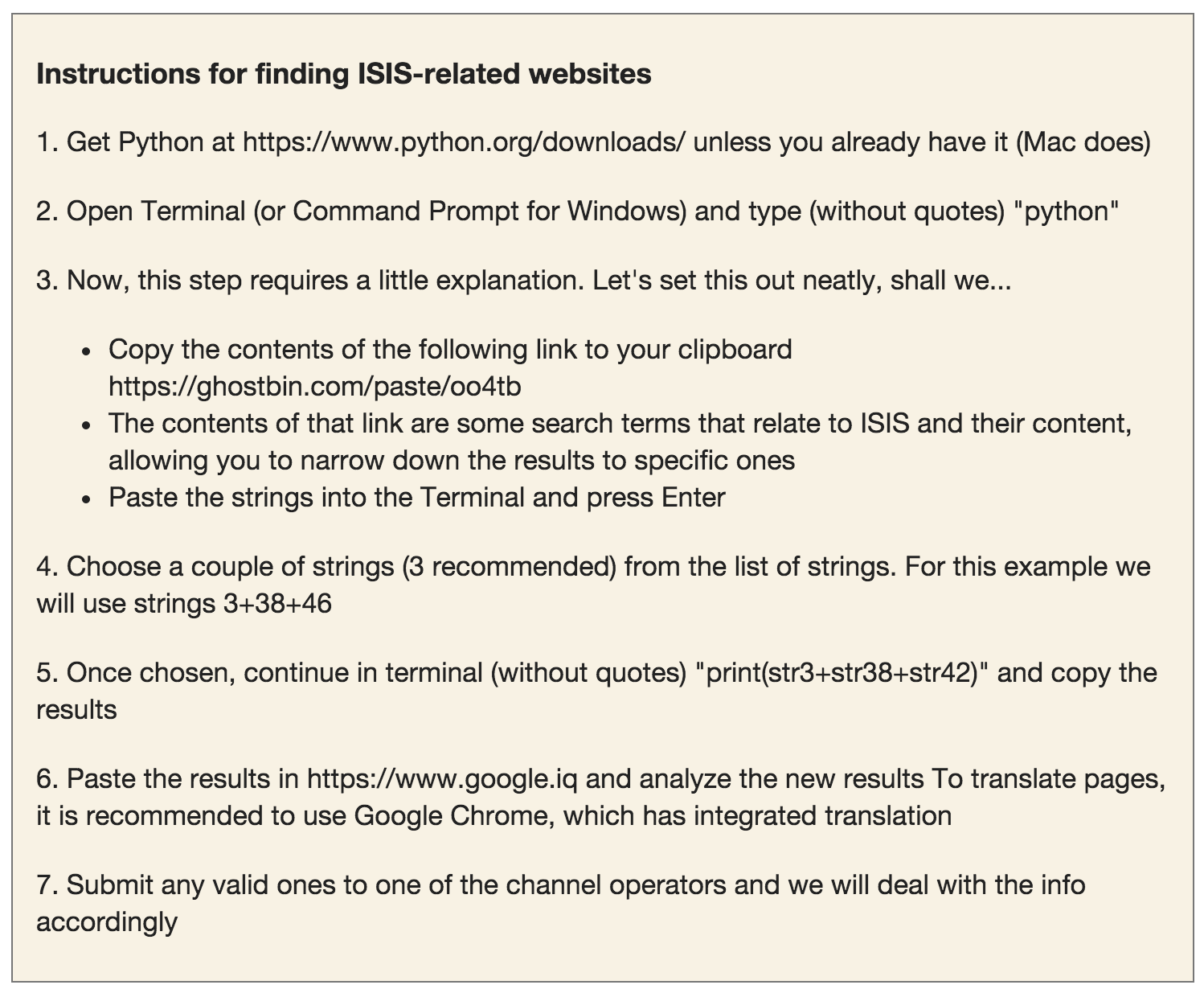
The deconstruction of individual authorship is not only present in the avant-garde, but in hacker cultures as well. This belongs to the category of anti-art according to Kappanyos, but is just as relevant for performable instructions of action. Bürger ascribes the beginning of the negotiation of individual authorship to Duchamp’s signature mass-produced ready-mades. F/LOSS, Free/Libre Open Source Software culture, has existed since (and to some extent, because) software became protected intellectual property. It is the word-wide movement of creating software in developers communities with public source code. In the classical sense, software created this way has no single author, as many authors contribute to it freely, creating different versions and strands of the same program. According to Coleman, individualism and collectivism are both present in a constantly contradicting manner in F/LOSS culture.
In order to examine how the avant-garde and hacktivism resemble in operation and process, we may analyze hacktivist interventions along the process-oriented typology of the avant-garde artwork described by Kappanyos. We may as well dissect avant-garde processes by Jordan's novelty- complexity- and process-oriented hacking-typology.
Hacking Typology of Avant-garde Processes
As Schulte-Sasse and Kappanyos both point out, the art-making of the avant-garde is much more focused on methodology and process than on end product. In the following, I will examine how avant-garde processes may be understood within Jordan’s novelty-complexity- and process-oriented hacking typology.
As described above, novelty is of major importance to the reception of the avant-garde artwork: the level of novelty and creativity the artwork exhibits when first published. Such is the case with the 0-day exploits known in hacker cultures. A 0-day exploit is the exploit of a so far undiscovered vulnerability of a system, and it represents the highest value of intellectual achievement, creativity, and innovation in hacker subcultures. It is broadly perceived as excelling creative intellectual work (and is bought and sold on information security black markets accordingly).
Let's examine Duchamp's La Fontaine as a 0-day attack, slipping through a hole of the artistic canon's security protocol. In this case, the vulnerability is the novelty-hungriness of the bourgeois that instantly includes the piece in the canon for the idea of wanting to provoke it. Any further ready-made may be considered a 0+1-day in this regard, whereas the vulnerability is still present, and the results achieved with the same exploit, although less outstanding, are very similar.
Enlarge
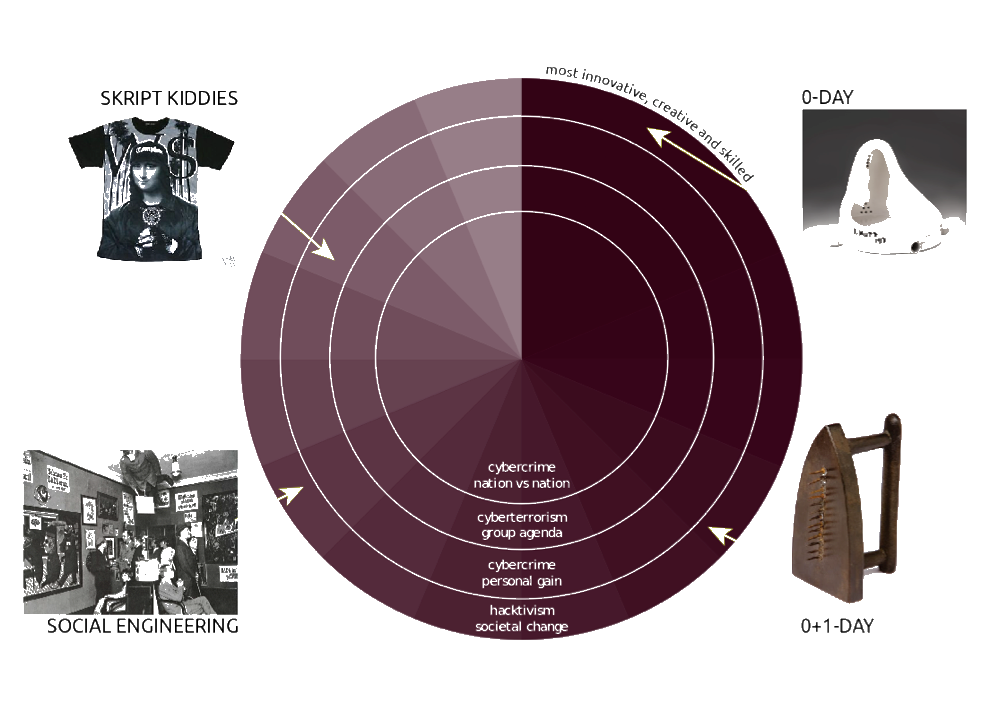
A rubber key-chain in a Parisian souvenir shop today, picturing the pissoir first appropriated by Duchamp shall, by no means, compare to the first presentation of La Fontaine. Not only because it is a cheap representation of it, but also because the level of novelty and creativity in the latter is nil. If we understand the first publication of La Fontaine as an original 0-day masterpiece, rubber key-chains are script kiddie level activities at most.
We may find numerous examples of social engineering as the hijack or misuse of common social conventions in DADA performances. The Grand Soirée organized in 1919, in Zurich's Saal zur Kaufleuten may serve as a good demonstration. The event reached its scandal-provoking peak with readings from Tristan Tzara and Walter Serner, which were indeed planned to provoke the audience against the performers. They definitely succeeded in doing so, getting the spectators involved in the event by throwing trash, money, and cigarettes towards the performing dadaists, preventing them from finishing their reading sessions, including Serner's Letzte Lockerung (Last Loosening). The screenplay anticipated the audience's reaction, building on the manipulation of social behavior.
Avant-garde Typology of Hacking Gestures
The reverse is the application of the process-typology of Kappanyos to phenomena of hacktivism. Kappanyos analyzes the destruction of the author's traditional relation to their own work of art as part of the avant-garde's anti-art component. He regards innovative processes to be at the core of the innovation of the avant-garde, instead of the artworks themselves. He identifies ephemeral, aleatoric, combinatorial, recontextualizing, self-referential and performative processes. In his interpretation, aleatoric gestures do away with the artist's implicit intention, the readymade excludes craft, and performance puts an end to artwork being a product solid in space and time. I will examine the presence of these processes in hacker culture to demonstrate how the framework available to interpret avant-garde artworks helps us understand hacker cultures.
Enlarge
Most hacks are definitely ephemeral by nature, as they last until repelled, and, when system administrators on the defense side are smart, they leave no trace, or the trace they leave is reversible. Much of the history of hacking is maintained through documentation as a result of the temporary nature of hacking actions. The actions themselves do not last, but they are kept alive by documentation in the subculture. For example, Operation Payback targeted opponents of internet piracy and banks withdrawing donations from Wikileaks in 2010 with DDoS attacks. The chain of events was over in three months, but it is well-documented in the history of hacking.
Looking at Free/Libre Software development, we see a general combinatorial method, working on several parts and versions of the same software, testing and improving each other's work via tracking versions and contributions in repositories. The TOR Project is an instance of privacy-guarding open source software developed by groups of people over time with different public versions.
Chance plays a role in many actions of hacker culture. Observing the operational strategies of Anonymous as described by Coleman, one might marvel at how big of a factor chance is in a hacktivist operation. An attack may be pursued just because it is technically feasible, whether it islet that be or not be against a very specific target or a pick from a broad pool of antagonists. From the many potential attacks, the one that eventually can, will be pulled off. This is especially true in the case of trolling and the LulzSec collective. Many attempts of attacks do not turn out to be successful, whereas some reach unintended targets. Therefore, intended chance or the intent of chance is present in hacktivism. A prominent example of a chance-based 0-day exploit from the seventies is the becoming of the famous phreaker Captain Crunch. John Draper discovered that a certain toy found in a cereal box makes a sound exactly the same as the frequency triggering US long-distance calls. Draper became a cult hero for this discovery among fellow phreakers (Author’s note: Phreakers or phone freakers are early phone hackers).
Enlarge

Recontextualization is central to hacker culture, as it transgresses and sometimes even demolishes borders of institutional and private, state and civilian, commercial and anti-consumerist information technologies. The list of examples is endless, but the genre of leaking and doxxing are probably the best of those in terms of recontextualization. Wikileaks’ Iraq War Leak of 2010, including the video now famous as ‘Collateral Damage’, may be regarded as a recontextualizing hack, as, by making data public, it led to questioning the actions of the US authorities and military in the Iraq war.
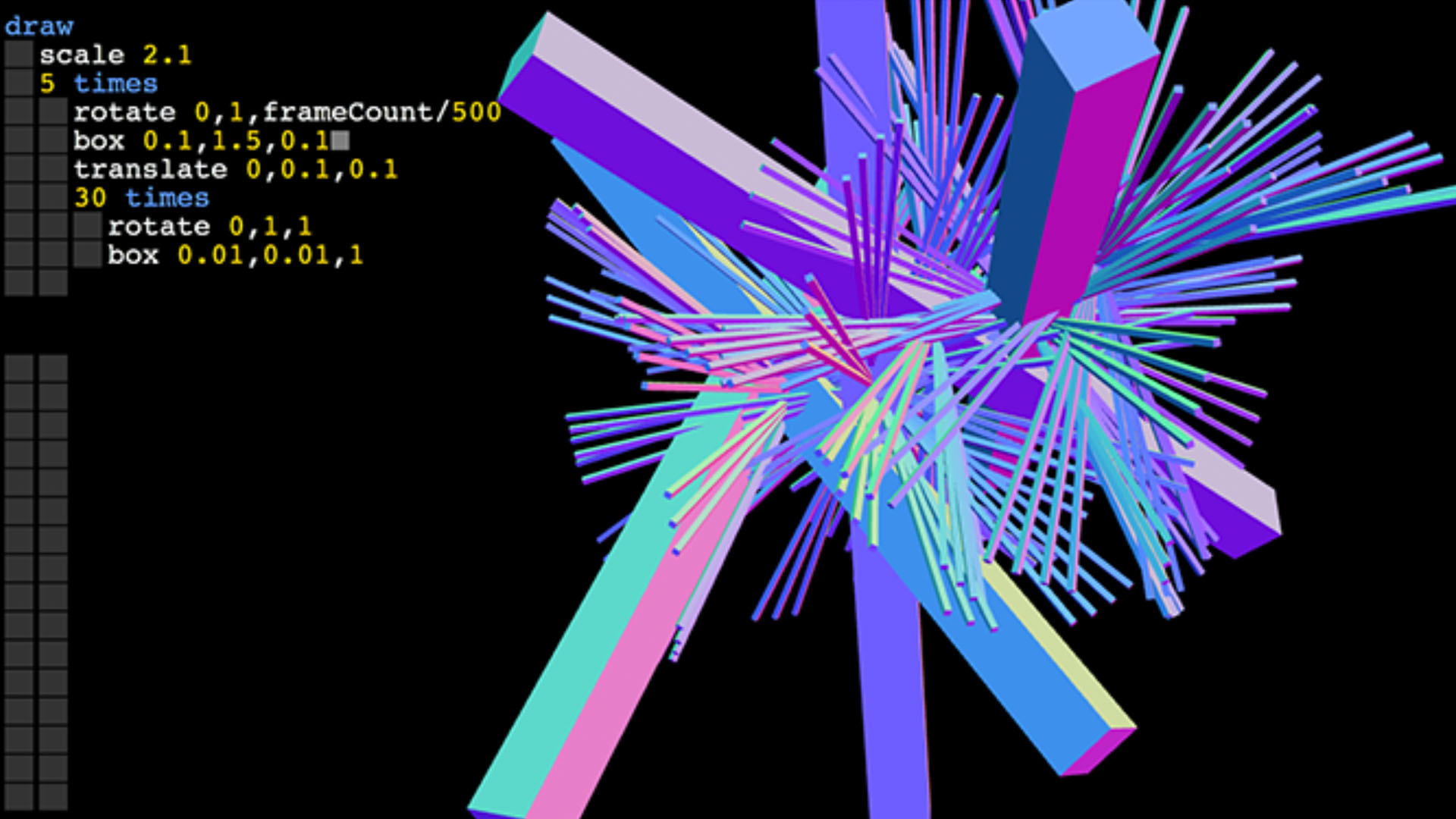
One of the sophisticated self-referential phenomena of hacker culture is live coding: a digital performance where one writes a code that generates an image or animation, and both the code itself and the generated imagery is shown on the same projection screen. This way, not only the aesthetics and complexity of the generated animation, but the wit and craft, and even the possible humor of the written code generating it, might be observed. Exploits with signatures of their authors are on the opposite ledge of the self-referential creativity range: A targeted website or server may be down while the signature of the hacker appears on the same URL.
Enlarge
Performativity, as the overcoming of the artwork's mediated character might be the single one aspect of the avant-garde that hacker culture does not deliver, if we understand it as an elimination of mediation. If by exceeding mediation we mean overcoming the character of the medium, it might be considered a very valid factor. When the open culture activist Aaron Swartz wrote a script that downloaded thousands of paywall articles from JSTOR through MIT’s library access, he was definitely overcoming the limitations of the medium, as it was designed for manual use only.
The existing theoretical framework available to analyze the traditions of avant-garde art can provide valuable new aspects to understand hacker cultures and hacktivism. As most theoreticians point out, the historical avant-garde, in contrast with its declared intent, did not destroy the institution of art as a whole, nor did it erase traditional genres of art, but carried out interventions that changed the tradition of art forever. Similarly, hacker culture did not destroy information society as such, but its contribution to shaping techno-societal relationships is of substantial importance.
The Influence of Anarchism
What a hacker does and will do is embarrass the power elite as dudes on the ground can’t (…) by puncturing the illusion of power. Prof. Peter Ludlow
Anarchist ideology inspired the artists of the avant-garde. Patricia Leighten wrote about the influence of anarchism on the pre-war Paris art scene. She points out how individualist anarchism was appreciated by many artists of the era for enabling them to work more freely and less according to tradition. Roger Farr examines Hugo Ball’s commitment to anarchism in the period of the Cabaret Voltaire being active in Zurich. According to Farr, Ball’s reflection of the collectivist Bakunin’s writings proves that Bakunin’s ideas on destruction as an act of creation and his criticism of language as a tool in the hands of power influenced Ball’s Zurich activities instrumentally.
Anarchist ideology inspires contemporary activist struggles, as well as it affects much of their practical, operational and public tactics. Decentralization and autonomy, the equal share of agency between members of a community, affinity based work groups are cornerstones of anarchist ethics. Anarchist communities practice decision-making methods fairly unknown to the wider public, such as consent, cooperation without agreement, unauthorized direct action, mostly in small groups whose members work for the same goals. The following remarks point out patterns of anarchist ideology in the history of hacker culture.
The system-architecture of the Internet collides with how anarchism envisions communities: a decentralized network of nodes which operate without a controlling hierarchy, forming a dynamic network with each other, and reorganizing themselves if needed. In the case of the World Wide Web, nodes are servers, while in the case of anarchism, nodes are syndicates, collectives, affinity-groups or work-groups. Both systems are non-hierarchical and decentralized by design, therefore the loss of a node does not affect the overall performance of the network, and the nodes are free to reconnect in different constellations. If we examine the birth of this system architecture in a historical context, Stewart Brand’s Whole Earth Catalog appears to be of major influence. The Catalog formed an open information network connecting colonies, cities, reserves and other actors in accordance with the West Coast Zeitgeist of the late sixties. It is definitive that the architecture of the World Wide Web and anarchist methods of operation are reflecting each other, and that the former is used by all known contemporary activist struggles.
Eric S. Raymond, editor of the hacker Jargon File claims to be an anarchist. Steven Levy points out that MIT’s AI Lab was operating on principles of anarchism. An Anarchist’s Guide to Free Software explains in detail to less technically prepared anarchists why F/LOSS is the sole acceptable choice of software for an activist critical of capitalism and globalization. The original hacker ethic echoes the ideology of anarchism in direct access, the questioning of authority, and by being anti-bureaucratic.
Webs of Activism
Tim Jordan examines the latest participatory turn that followed the fall of the Berlin Wall (also identified by Bishop in the context of art) in his book Activism!. He points out that the activism of the millennium is relieved of the rhetoric of the class struggle, and organizes along a new set of values in a horizontal manner, where these values are not exclusive to each other. These groups share an anti-globalist, oftentimes anti-capitalist, leftist, anti-machist and non-violent agenda. Anonymous represents part of the post-9/11 wave of this generation, and serves as a great example of information technology shaping operational strategies that reflect the principles of anarchism in digital space.
Anonymous consists of activists all over the world working for different goals, oftentimes independently, without each others’ consent or knowledge. There is no membership, permanent location or main goal, and not all who contribute possess high-level computer skills. The method of organizing, the tools of the actions, a few principles and the identity framework are common. Anonymous functions along the lines of doocracy, a shared work dynamic where everyone does what they prefer according to their interest and motivation. Work-groups are formed spontaneously and without solid borders; fluctuation between and from and to groups is constant. Debates do not necessarily end with agreement, but sometimes with the acceptance of non-agreement. In spite of the fact that many prominent members are currently serving sentences, Anonymous is an important actor of the activist scene: it mostly works in defense of information freedom and people’s privacy, as a sort of self-authorized public service justice organization protecting civilian rights in the digital realm.
Coleman understands the public identity of Anonymous as a collective identity. This is, on one hand, the continuation of the golden era hacker gang names, but also rooted in neo-avant-garde tradition. Tatiana Bazzichelli marks several grassroots groups of this collective identity tradition as cultural forerunners of Anonymous in her book Networked Disruption, such as the Luther Blisset Project, Neoism, the Church of the SubGenius and the Italian Anna Adamolo movement. Bazzichelli understands these groups as part of a shared network modality tradition, where the groups come from different contexts and goals, but do share a grassroots network structure, which, just like mail art, according to Bazzichelli, created new, free patterns of communication for many art movements from DADA to Fluxus. Brian Holmes takes the liberating power of collective identities further: he claims that free identities like the Luther Blisset Project created prototypes of media subversion, that made the emergence of transnational activist movements possible by the millennium.
Code as Speech
‘
The word has become a commodity (…) We must give up writing second-hand: that is, accepting words (to say nothing of sentences) that are not newly invented for our own use. Hugo Ball
Hacker culture and the historical avant-garde share a stark skepticism and deconstructive attitude towards language, given that we understand code as language. Coleman, in her book Coding Freedom, claims that source code may be understood within the category of speech, and thus shall be legally protected as free speech. The 5th statement of the Hacker Ethic claims that one can create art and beauty on a computer. Contemplating these statements one may look at hacking as the overcoming of the semantic determinations of software. We may analyze hacking as an intervention that hijacks meaning (function) of text (code). We may find yet another analogy with avant-garde art in its skeptical, deconstructive attitude towards traditions of language and forms of literature as parts of the institutionalized status quo. This requires a bit of explanation.
A programming language is an artificial, human-made, electronic language that has a fixed syntactic set of rules. Code written in such language is a set of commands to be executed by a computer. The author of a piece of software composes a text (code) in a high-level language, where this text (code) consists of a series of logical operations, and is called the source code of that software. This source code is compiled by that language as an application, translating its operations into assembly, then to machine language for the computer to execute. The vocabulary of most high-level languages consists of mathematical signs and words of the English language.
This short intermezzo shows that each software is a particular artificial linguistic construct, that is meant to transmit information between human and machine or machine and machine. Each family of programming languages has different syntax systems, while, within a single family of languages the subgroups are understood differently as in the case of human languages. In this interpretation text is the source code of software to which a particular set of syntax rules apply. The meaning of a source code is the function of the software compiled by it. Being skeptical towards language, the deconstruction of semantic, literal, poetic norms present in the avant-garde concurs with the deconstruction of the functionality, or the meaning of software.
We may regard hacking gestures that hijack or impair a functioning communication system by coding as a semantic intervention. We have to remember that the hijack still has to happen within the syntax of the given language in question in order to function as such. The destructive semantic interventions of hacker culture resembles the avant-garde’s relationship to language. The skepticism towards the status quo of language is, in both instances, induced by the submission of that given language to the institutional power structure.
Presently, the avant-garde ideology of hacker culture is most genuinely expressed in the FROM DADA TO DATA manifesto published by the former MOTI, Museum of the Image, in 2017. Among the many prominent authors of this critical and satirical publication we find Mieke Gerritzen, Geert Lovink, Bruce Sterling, and McKenzie Wark. The manifesto quotes Kurt Schwitters claiming that it is not DADA that produces nonsense textuality, but reality controlled by authoritarian institutions and capital. For Dadaism, lovemaking and lawmaking with the same set of words is absurd. Bürger and Kappanyos both point out that the relationship of the avant-garde with language depends closely on its relationship to society and to the institutions of art.
On the 100th anniversary of the Cabaret Voltaire, the Dataist Manifesto calls for a new Dadaism in the 21st century over-saturated by digital data. The new Dadaism shall be Dataism. Dataism calls against embracing Big Data and the controlled communication provided by contemporary information technologies, and highlights the lack of societal consent over surveillance and control technologies already in practice. It criticizes maker culture for not being critical, and it expresses solidarity towards the hardship of artistic production.
In an article that briefly precedes the Dataist manifesto, Lovink already invited radical thinkers to question authoritarianism in the online world: he claims that ‘[w]e need to remain rigorous and ruthless and demand avant-garde experimentation at the highest level and live art forms that express the feeling of our era’. Dataists, independent programmers and artist-hackers who resist the powers that control the Web, demand a new, 21st century art: independent programmers and artist-hackers who resist the powers that control the Web. They claim that programming is the new painting and writing that finally ends the cult of the author for good.
Good practices
Before concluding the investigation of how the historical avant-garde and hacker cultures are connected, it is worth looking at a few great examples of correlation: artworks from the last two decades’ techno-critical, subversive new media scene that do not only comply with the definition of hacktivism as transgressive gestures, but represent aesthetic and sensory authenticity as well, fulfilling the demand of DATA TO DADA’s aesthetics and ethics. I dare to recommend these transgressive works that I understand to fulfill the dataist manifesto’s objectives as worthy of close observation.
Enlarge

Heath Bunting.
In 2000, Heath Bunting spent seven months crossing Europe’s borders illegally by foot, and documented, then published the full process as a manual. He listed the necessary equipment, tools, sources of food and help, as well as the expected difficulties. One can only view ‘Border Xing’ from an IP outside the EU. Bunting, an ascetic net:art pioneer of the nineties, experiments with building low-tech communication systems that aim to be open and egalitarian. Most of his works walk over borders of consensual power structures. ‘Border Xing’, completed with Kayle Brandon in 2000, is probably the most prominent example of ambition. In the age of biometric passports, RFID chips, international highways and integrated circling databases, network technology defines the methods of surveillance. The simple act of walking through borders, in such context, is a revolutionary act. Bunting and Brandon refuse to contribute to the methods of surveillance with this experience, rather, they create their own accessible micro-database, that works in opposition to official ones. Doing this as backpackers and DIY media activists does not only ignore any of the aforementioned formal powers, but ridicules them out right by not requesting a dialogue with them.
Enlarge

Tanja Ostojic. Photo by: Rupert Larl.
In a project concluded in 2005, Tanja Ostojic (citizen of the then non-EU member country of Serbia) used the image of her body online in ‘Looking for a Husband with EU Passport’. The now defunct website pictured Ostojic naked, without any hair, stating that she is looking for a husband with an EU passport. Objectifying her body for her own means, instead of the state’s, men’s or anyone else’s, Ostojic made a brave statement. After receiving numerous applications, she married a German artist, whom she later divorced, and created an exhibition of the process, including the application letters and the wedding ceremony. Her project thematizes the commodification of the female body during a turn in digital commerce when that same female body joins the arena of online goods. Ostojic currently lives in Berlin, Germany.
Enlarge

!Mediengruppe Bitnik.
Enlarge

!Mediengruppe Bitnik.
A decade later, in 2016, the Swiss art duo !Mediengruppe Bitnik published the Random Darknet Shopper, an online shopping bot with a weekly budget of 100 dollars. The bot chose and purchased random products from the deep web, with the resulting packages exhibited in a St. Gallen gallery. The shipments were received and loaded into the empty display boxes of the exhibition space by the gallery staff. Among the shipments were fake branded goods, non-taxed cigarettes, a Hungarian passport and a packet of MDMA. When the Swiss authorities wanted to arrest whoever was responsible for the purchase of the latter, they faced an unexpected problem: how do you arrest an algorithm? After two months of press attention and debates, the algorithm was released and continues its activities until this very day. This project shows more than one eerie aspect of our digital lives: however accustomed we are to robots serving us, we are still very unprepared for them making decisions for themselves; this is demonstrated in an ever sharper light when the methodology of decision does not stick to any set of values but is fully randomized; on top of this, the program goes shopping on the dark web, a medium unusual and startling by itself.
Conclusion
Hacktivist art has amazing potential for transgression and it’s time we talked more about it and understood it better. Non-conformist information technologies are probably the most inspiring layer of contemporary culture to study, as they have way more effect on shaping this culture than what one would think at first sight.
The immediacy, innovation, subversion, and operation methodologies that are present in these phenomena might rejuvenate contemporary artistic practices and their interpretation. This text hopes to contribute to the inception, reservation, and understanding of such subversive attitudes.
Juli Laczkó is an intermedia artist engaged with critical research in visual arts and digital culture. She holds a practice-based doctoral degree from the Hungarian University of Fine Arts for her research on “Strategic Interactions between Hacker Culture and Contemporary Visual Arts”. Her doctoral dissertation is currently being prepared for publication in English and Hungarian. Her artistic research is informed by the intersection of visual arts and hacker culture, focusing on articulating ‘intermediality’ in space. Juli lives in Amsterdam and teaches at the Image and Media Technology program at the Hogeschool voor de Kunsten Utrecht.
Reference List
Bazzichelli, Tatiana. Networked Disruption: Rethinking Oppositions in Art, Hacktivism and the Business of Social Networking, PhD diss., Aarhus University, Aarhus, 2011.
Bishop, Claire. Artificial Hells: Participatory Art and the Politics of Spectatorship, London: Verso, 2012.
Coleman, Gabriella. Coding Freedom: The Ethics and Aesthetics of Hacking. Princeton: Princeton University Press, 2013.
Coleman, Gabriella. Hacker, Hoaxer, Whistleblower, Spy: The Many Faces of Anonymous, London: Verso, 2014.
DC Radical Tech Collective. An Anarchist’s Guide to Free Software, 2009, https://we.riseup.net/rtc/an-anarchist-s-guide-to-free-software+34940.
Farr, Roger. “Poetic License: Hugo Ball, the anarchist avant-garde, and us”, in Jeff Shantz (ed.) A Creative Passion: Anarchism and Culture, Cambridge Scholars Publishing, 2010.
Gerritzen, Mieke et al. FROM DATA TO DADA, MOTI Visual Culture Paper Special Edition, Breda: MOTI, Museum of the Image, 2016/2017.
Hagen, Wolfgang. “The Style of Sources: Remarks on the Theory and History of Programming Languages”, in Wendy Hui Kyong Chun and Thomas Keenan (eds.) Old Media, New Media: A History and Theory Reader, New York: Routledge, 2006.
Himanen, Pekka. The Hacker Ethic and the Spirit of the Information Age, New York: Random House, 2001.
Jones, Bryan. “The Punks of Pirate Bay: An Anarcho-Analysis of File-sharing Websites” in Jeff Shantz (ed.) Creative Passion: Anarchism and Culture, Cambridge, UK: Cambridge Scholars Publishing, 2010.
Jordan, Tim. Activism! Direct Action, Hacktivism, and the Future of Society, London: Reaktion, 2002.
Jordan, Tim. Hacking: Digital Media and Technological Determinism, Cambridge, UK: Polity. 2008.
Kappanyos, András. Tánc az élen: Ötletek az avantgárdról, Budapest: Balassi, 2008.
Krauss, Rosalind. The Originality of the Avant-Garde and Other Modern Myths, Cambridge, MA: MIT Press, 1986.
Leighten, Patricia. The Liberation of Painting: Modernism and Anarchism in Avant-Guerre Paris. Chicago: University of Chicago Press, 2013.
Levy, Steven. Hackers, Heroes of the Computer Revolution, 25th Anniversary Edition, California, US. O’Reilly, 2010.
Moody, Glyn. Rebel Code: Linux and the Open Source Revolution. New York: Basic Books, 2001.
Raymond , Eric S. (ed.) THE JARGON FILE: The New Hacker’s Dictionary, 3rd edition, n.d., http://www.catb.org/jargon/html/.
Raymond, Eric S. A Brief History of Hackerdom, 2000, http://www.catb.org/esr/writings/homesteading/hacker-history/.
Schulte-Sasse, Joachim. Foreword, in Peter Bürger, The Theory of the Avant-Garde, trans. Michael Shaw, Minneapolis: University of Minnesota Press, 1984.