With the advent of platform centralization and the defeat of an autonomous internet, the question of strategies of resistance becomes even more crucial. How do you organize all the different tactics that have emerged in the last decades? Where do you store them? How do you maintain them? We start the last session of the first day as a dive into the more complicated political questions: how to reclaim the internet and organize ourselves collectively in this undertaking, featuring four different presentations. Before handing the microphone to our speakers, Tommaso argues the event to be part of a tentative in building alternative tactics, and raises the preliminary condition for its success: gathering tactical knowledge about platforms and bringing it together. This is the only way to “move from tactics to strategies”, from the user to the collective misappropriation.
LURK: Jenga Computing and Precipice Workflow, Aymeric Mansoux
Aymeric Mansoux first comes to the stage, with a lot of technical preoccupations as part of his “half-improvised” presentation. “Jenga computing and precipice workflow” is the title of his intervention, announcing to the audience the complicated situation in which alternative infrastructure tries to survive. How to bring about a sustainable mode of workflows, to maintain these autonomous technical infrastructures that we cherish and praise in theory, yet hardly work on sustaining, or even deploying, in practice? Aymeric makes a disclaimer from the start: he will mention infrastructure a lot (that is, servers) and how to deal with them. He will only talk about the context of northern-western Europe, starting from his own experiences with Lurk, which he started with Alex McLean in 2014 as an “independent e-mail and web discussion platform for computational culture”. Lurk is “an infrastructure which facilitates and archives discussion”, from mailing list hosting to streaming, chat and access to the Fediverse via Mastodont. Through the history of Lurk, Aymeric aims to expose both a “hopeful?” techno-cultural perspective (or at least possibilities) and a “bleak?” socio-economic context. The idea for Aymeric, it seems, is to shake us in regards to the too-often neglected aspects of alternative infrastructures – of the economic condition in which they try to survive, and of the actual cultural practices, which do not necessarily tie back to our discourses about them.
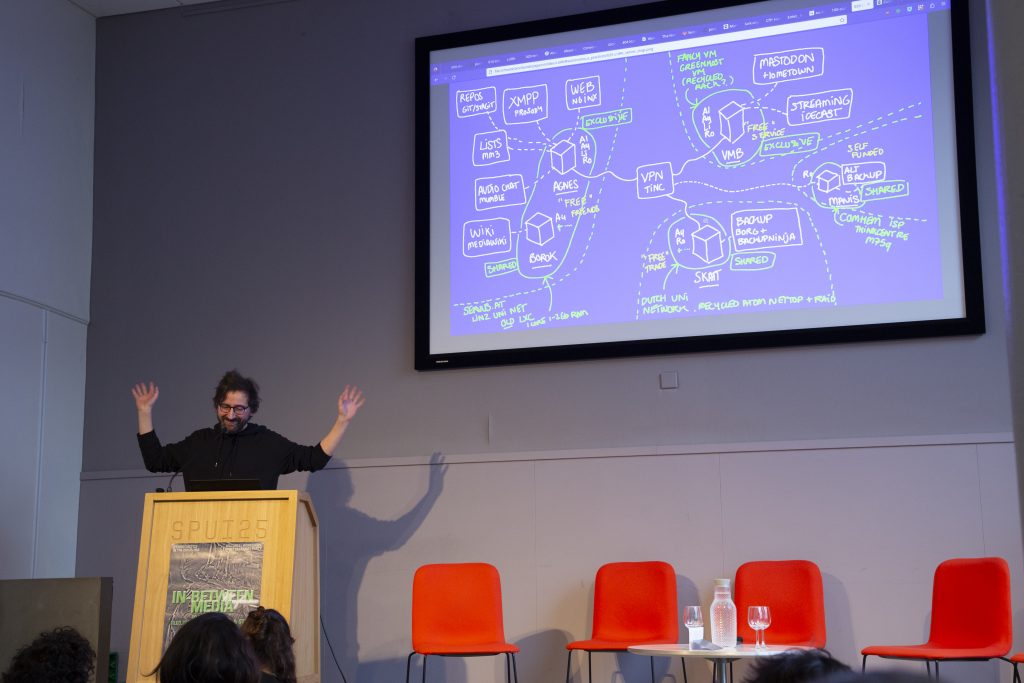
Aymeric Mansoux and Lurk’s server map.
“By 2014, everyone has given up on critical, alternative infrastructure”, he recalls. “People moved to the ‘user condition’, about what we can do with our own data, …”. At the same time, some were pleading to “bring back mailing lists, to bring back discussions to a system [they] can own”, and then archive. “By 2017-2018, we were getting tired [in the alternative infrastructure ecosystem], fed up with everything”. Aymeric talks about “admin burnout”, which is a notion that I, and probably many other digital workers in the room, can relate to. Yet parallel to this exhaustion, was a collective excitement as to alternatives such as Mastodont, the Fediverse, which revived the discussion at the time. During the Covid years, Lurk had time to consolidate and deploy things. Aymeric tells us about this “eureka” moment of his, recently: “what we are going on is not a repeat of 10-15 years ago!”. This is the “Musk-Twitter” moment, which can be described as such: “Lurk is composed of people not so much engaging in sharing infrastructure and software, as it is of a community that wants to participate in an infrastructure of healthy, sensical discussion.” 2000 people subscribed to over 60 mailing lists, a maximum of 666 people on the Mastodont instance, and 400 external people using Lurk’s chatrooms. “It is small compared to Twitter, but still significant for us”. However, “a lot of work is needed to not have it collapse”, it is not just “magically working” (this phenomenon of relating to technology as if it was working by magic, seems to summarize well the situation Aymeric wants to decry). A lot of humor is invoked to partly dispel the weight of responsibilities that comes with Aymeric’s presentation. Community servers become a “dinosaur story”: “why did they disappear? they were so powerful!” says Aymeric to a laughing audience. However “there are many obvious reasons as to why they are hard to maintain…”
To conclude, Aymeric reminds us of the material complications driven by the socio-economic context we are living in, starting with the price of the rent that almost doubled: “this has an impact on what you can do, develop”. As he explains, “we started Lurk because we were old and privileged enough to do it as a side job”. Now, “Lurk is constantly on the precipice of the socio-economic situation” (starting with inflation). How can we run infrastructure sustainably in our context? Having these kinds of side jobs is increasingly difficult. For Lurk’s free hosting services, they need to find at least 400 euros per month, just to run and maintain it. “How do we invite people to a nightmare of maintaining infrastructure without getting paid?”. Aymeric talks about the frustration in the work done by people involved in alternative servers. A work full of struggles. We need to “go beyond an academic understanding of infrastructure”, and stop the exploitation of people maintaining technology. “The only way around it is the individual contribution of the person”, he believes. With a workflow constantly on the brink of the precipice, to having the infrastructure collapse, “everybody is an entrepreneur, nobody is safe”, as he explains by displaying the book of the same title on-screen. “There is not much talk and writing on the precarity of the cultural sector, the ‘entreprecariat’”. For him, beyond the easier and better-known questions of cultural, political, and ecological issues of infrastructure, we need to start paying more attention to its actual technical aspects, in terms of maintenance.
How-to.computer: A Self-Hosting Guide, Lukas Engelhardt
We move on to Lukas Engelhardt’s “how-to.computer: a self-hosting guide” presentation, which he disclaims as “some naïve optimism to counterbalance the previous talk”. Lukas is a graphic designer that stopped using centralized servers in his workflow and engages with their very materiality. “How do they look, and feel? How are they maintained, by who?”, he starts by asking. Through his “manual”, Lukas wants to make people build their own servers, to “stop using dropbox”. Practice is at focus here: “we criticize Big Tech, which is important, but then we use Microsoft Teams, Google Docs, Gmail… it is difficult to make the switch”, even for hackers, even for cultural institutions aware of the issues of using Big Tech technologies. There are “ethical considerations when using software: such as energy, exploitation of workers, government surveillance, …”. On the other hand, alternatives often remain hypothetical, and are often not “production ready”.
So it is all too often tempting to go on “the cloud”. “The cloud is only present, dominates the internet, and people don’t know what to do about it. How to drop it back to the ground? The cloud is out of reach, or seemingly unreachable”. Lukas has just played a 2-minute hilarious video of someone shouting at a cloud, trying to make it magically disappear in front of him – repeating frantically and in different tones (in case one of them has more effect on the cloud) “kleee disappear! Kleeee disappear! Kleee disappear!” Facing such an out-of-reach cloud, it indeed seems to us that only a mystical approach of incantations can make it dissolve. This makes me think of people desperately dancing together for the rain to come, except that here, it is shouting alone at a cloud to make it disappear. The cloud, be it atmospheric or as a metaphor for digital servers, does indeed have a mystical resonance with us: a power we desperately try to seize, but that is beyond our actual will. The cloud is a fuzzy term, explains Lukas: it is “the rest of the internet”, out of control for the majority of people. “That is why the term was chosen of course: it is mysterious, unknown by definition”. Yet, quite paradoxically, the cloud “is just someone else’s computer”, as he simplifies through a t-shirt image with that catchy explanation. When we give data to “the cloud”, we don’t control the terms and conditions of our data – “there is nobody to talk to if something goes wrong” (such as when data disappears). How come it is so seductive to us, then? “People expect things to work immediately, without delays”. This is what Lukas calls the “cloud narrative”: “things should always seem light, easy, and anything that betrays this principle betrays the façade image of a cloud”. From this narrative and its related practices, “we are spoiled, used to have 99,9% constantly smoothly available”.

Lukas Engelhardt in conversation with Tommaso Campagna.
Can we learn from the squatting movement, when it comes to network activism and spreading the practices? Lukas tries to make a connection between the squatting movement and the hacker culture, historically present in the Netherlands. “‘Cracking’ was used for ‘hacking’”, he recalls. Could we engage digitally in “temporary autonomous zones”? We can also learn from feminist theory: that is, a “space run from a community that has enough motives to take care of it”. Instead of seeing this caring time as a lost time, we should start seeing it as an essential time for community-making. Someone in the audience tries to challenge Lukas’ analogy, by asking where is the political in self-hosting, as opposed to claiming an actual space. Lukas admits that the analogy of space does not always hold, as there is not the same direct conflict and competition in digital space as there is in a more physical one, such as a house. For Tommaso, bouncing on this comment, it is actually possible to squat data centers: “as we do at the INC, to take a very personal experience”. Geert then argues that be it in a physical or digital space, “without self-organization, nothing happens”.
The Tactical Misuse of Online Platforms, Nick Briz
As we move on to the third intervention of the session, and as we get emotionally drained by these different displays of our collective disempowerment by Big Tech or the socio-economic situation, nothing could be timelier than Nick Briz’ presentation on “the tactical misuse of online platforms”. Even though it must be noted that he appears to us through Microsoft Teams, which makes the audience giggle, especially as he struggles to share his screen. People tell him to check if “he has all the rights”, Chloe tries to make him an “attendee”, then a “presenter”, … until finally, Nick realizes: “ah, it is the ‘share’ button!”. He must not use platforms quite often indeed. Nick is about to tell us how to misuse platforms designed to use us – that is, designed to collect our data, to train an algorithm able to predict our behavior and manipulate it accordingly. An attempt at tactics of online privacy, in the context of surveillance capitalism. As he explains, platforms “don’t need so much data to manipulate us!”. As for Uber, for instance, they just need to extract battery data, “which they exploit to charge higher fees”. This single data extraction allows them to manipulate our behaviors, when we are anxious with low batteries on our phones – which they use against us, bypassing our awareness of it. But his presentation is not about displaying all of these manipulations’ techniques, quite the contrary: it is about counter-manipulating platforms that are based on the manipulation of our behaviors. Because if platforms can manipulate us without our awareness and consent, this might as well apply the other way around. Here comes the crash course.

Nick Briz in a hybrid presentation setting.
There is one underestimated, simple way through which to misuse the platforms: the web browser through which we access them. Nick’s website contains “a collection of creative & experimental ways of using the browser to engage w/online platforms in a manner that undermines the exploitative algorithms + dark patterns designed by the data barons of surveillance capitalism”, which he encourages to use after his presentation. At the core of it, explains Nick, is the idea of “not using any interface of platforms in the ways they are designed to” – no button clicks, only the browser’s interface. While platforms like Instagram constrain us to log in, to access an image, for instance, we can simply use the “open link in new tab” option of the browser to subvert the mechanism.We can also use the “inspect” tool of the browser through a right click, usually used to debug, but which can be misused in tactical ends. Through this feature, we can manipulate the code of the website and platform, to go beyond the “blur” screens of surveillance capitalism (Nick de-activates in front of us the <div> element of the Instagram page responsible for blurring the picture unless you are logged in). For more experienced tactical misusers, the console tab allows us to inject our own code. Through it, we can remove all the metrics of Twitter, and remove Google services from its search results — scripts are directly available on the website to use, and we don’t have to write them ourselves.
It is a nice feeling for the audience to have these very practical, small – though not insignificant – perspectives to tactically misuse Big Tech right now. These “little hacks” are accessible enough to everyone to “mess with, hack, play” the constraining surveillance code of Silicon Valley’s giants. They go “from simple to proficient hacks”, some that any user can do. In answer to a question from the audience, Nick expresses the responsibility for a more competent programmer to pre-make hacks and make them accessible to a less-knowledgeable public, that doesn’t have the time and energy to learn to program. And finishes with this opening: can we tactically misuse Chat-GPT? As he explains, through this kind of generative AI, “the entry barrier is getting lower and lower” to generate functional code and scripts, that we can just copy-paste for our own tactical ends.
On Tactical Video Archives, Donatella Della Ratta
We finally arrive at the last session of the day, by Donatella Della Ratta, on tactical video archives. As she plays an amateur video of what seems to be a conference in Syria, in the early 2010s and during the insurrection, we get the feeling that we are getting back to “dark academia.” The speaker in the video explains how “YouTube is a necessary tool to reach international media.” But no, this won’t be a boring academic presentation to end the day. As the sound of the man’s speech fades, and ambient music makes its appearance in a frantic rhythm, evoking the battlefield and its harshness, Donatella starts her narration in such a way that, despite being the end of the day, it catches everybody’s attention by surprise. “It is September 2011, a few months before the Arab spring. I am reporting for the creative commons.” While the Syrian regime kills activists, she attempts to get a migrant to Warsaw safely by getting him a visa. Syrians gather “the image evidence”, in the words of Georges Didi-Huberman, “to prove the crimes committed against humanity”. “I fear for my life, I also fear for the life of these images” Donatella recalls hearing. In this context, the “social web” was needed for archiving. “War became a mundane activity, routine labor, a source of income” she narrates. Yet, “pixelated, blurry videos of the aftermath of the uprising was no more enough for the international public”. Clips became no more representational but “performative utterances”, communiqués of soldiers in Syria. In one night, all of the many images disappeared from the YouTube platform. This was the end of the belief for videographers that “things are going to be out there forever”. “I was convinced that Youtube was like my memory” Donatella recalls hearing. Yet, what you lose on Youtube, you never get back.

Donatella Della Ratta on tactical video archives.
Activists have forgotten or ignored the need for the local copy of files, or to archive their footage on alternative video platforms. Of course, this can be explained by “the urgency of the revolution in the making”. What was left? “Orphan images, with no makers, no sources, …” in the hands of people in Silicon Valley, knowing nothing of Syria. What do we make of activism today? Is there still a space of possibility for tactical media when it is controlled by tech giants? What has citizen journalism become in the era of TikTok? Visual culture now, according to Donatella, is a special case of vision, an exception to the rule. “At a time in which computation has become hegemonic, how do we build counter-hegemony, when images become hardly visible to the human eye?” This intersection between computation and images is of crucial political matter, she argues. We are feeding algorithms with data on how to identify places, and faces, to be reinjected as commodification into an algorithm. “All things human automated, now independent from the human eye. Our tactics have to shift in this context: activism has to focus not so much on producing counter-narratives, but rather in targeting the images of computational capitalism.”
As image and information flows are by design hidden in computation, what is most powerful: images or codes? Are coders or photographers more needed, in our context? According to Donatella, the Syrian rebels have shown us the importance of codes, beyond images. What we need now is a generation that thinks beyond the ideality of the image, as well as beyond “just an image”. We need to think about the image first and foremost by thinking about non-images, and their increasing roles in conditioning the former. Donatella finishes her speech, and the audience contemplates for one minute the consequences of all of these evolutions, as the ambient rhythm in the background fades out. Jordi asks: “After the photographer, who do we have now?”. We should work with coders, replies Donatella, make the effort to collaborate with them, or even code ourselves. “Networked images are operational images: it does not matter if they are true or false, but rather, how they circulate and how sticky they remain”. With these words, the first day of the In-Between Media conference ended, leaving the audience with a renewed sense of responsibility, well beyond the Syrian or Ukrainian battlefronts.